Emerging threats

We support organisations striving to build a trustworthy, safe online environment where users can engage authentically in their communities.
Cross-sector corporatesWe support international government organisations and NGOs working to provide infrastructure or improve the capabilities, security and resilience of their nation.
International programmes and developmentWe support commercial organisations operating in a digital world, seeking to protect their reputation and prevent business disruption caused by cyber attacks and compliance breaches.
UK government and public sectorWe support UK government organisations responsible for safeguarding critical infrastructure, preserving public trust, and maintaining national security.



We often get enquiries asking for a penetration test, but really the enquirer wants a vulnerability assessment (also referred to as a vulnerability scan). Conversely, many people ask for a vulnerability assessment when what they really need is a penetration test.
If these are different services, why is there so much confusion?
Many people use the two terms interchangeably, as they look similar from afar. However, up close it’s a very different story.
A vulnerability assessment is an automated scan used to identify vulnerabilities, while a penetration test is an in-depth attack simulation by experts, who actively exploit vulnerabilities to provide you a real-world understanding of your security posture against threat actors.
Let’s look at each option in more detail:
A vulnerability assessment is a system scan. It uses an automated tool to check for basic, known vulnerabilities. Imagine a burglar looking for and identifying a back entrance to your building, but not entering. The results of the scan will show how an application, website or other system is vulnerable, but it doesn’t provide details on what would happen if the vulnerability was exploited.
Many organisations choose vulnerability assessments to tick a box. However, there are limits to a vulnerability assessment because it can’t determine if those weaknesses are exploitable, or whether they pose significant threat to your organisation.
Penetration testing simulates real-world attacks a threat actor might attempt, analyses how difficult it would be to exploit the found vulnerabilities in your systems, and how significant the threat would be if the attack was successful. This helps your organisation to address critical risks before they can be leveraged by attackers. In our burglar scenario, this time they are checking for a back entrance and then actually entering the building (don’t worry, they have permission!).
This testing format is an examination of a network or system by qualified, experienced security experts who have been given permission to exploit the vulnerabilities and misconfigurations they find to determine their potential impact. The consultant will work to a defined test methodology to enter the network through the identified gaps (hence the term, ‘penetration’), using their knowledge, Open Source information, and a range of tools. Once gaps have been identified and tested in your systems and networks, they provide expert remediation advice to strengthen your security.
To more easily illustrate what is included in each service, we’ve put together this handy comparison of a vulnerability assessment and a generic penetration test (each test will depend upon the system being examined).
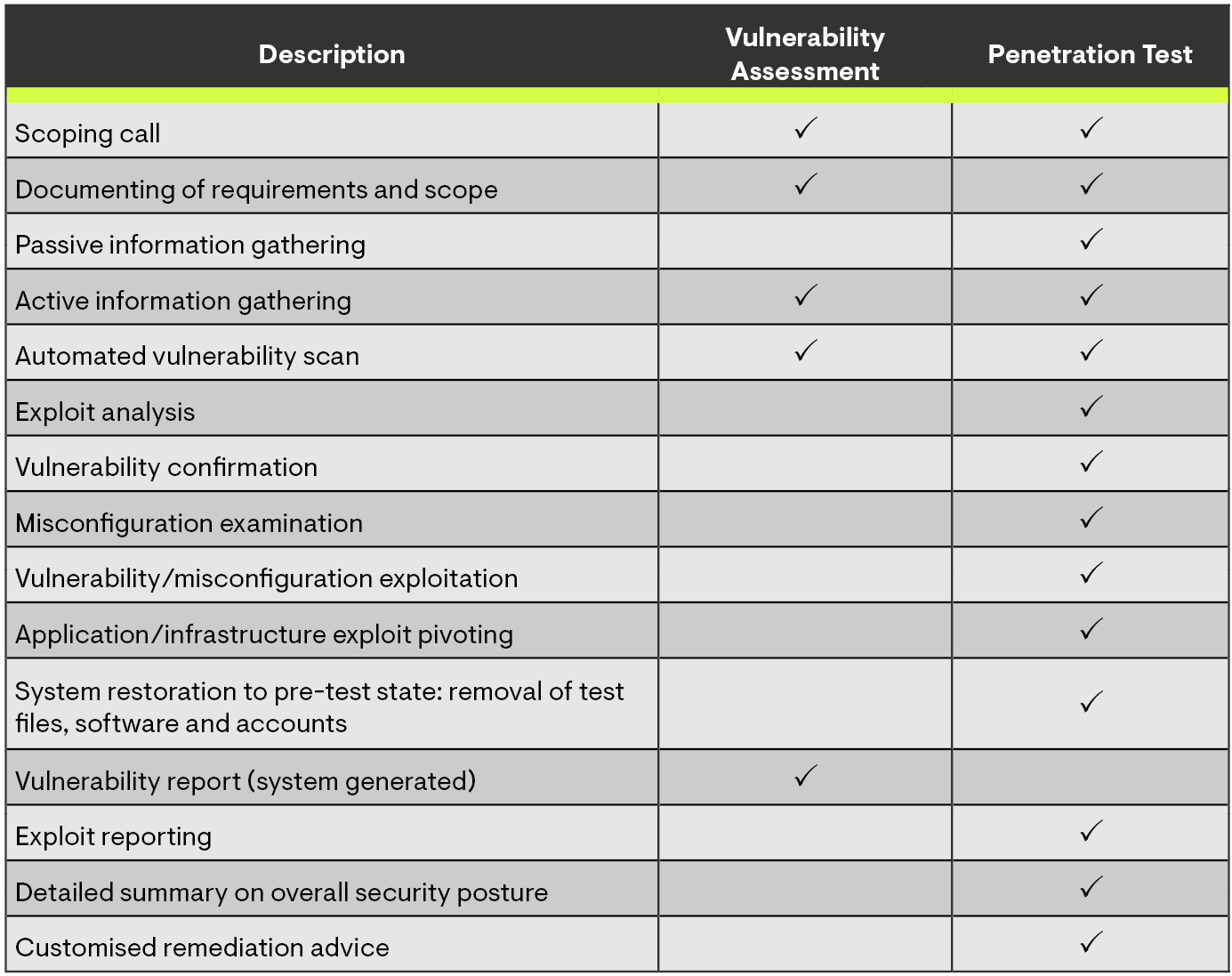
As you can see, a penetration test is significantly more in-depth than a vulnerability assessment. While a penetration test generally includes an initial automated vulnerability scan, it’s the manual exploitation of those vulnerabilities that requires a wide range of skills and time.
Think of a vulnerability assessment as a one-size-fits-all high-level automated scan that picks up the most common vulnerabilities. It’s cheaper and quicker because it isn’t resource intensive and is essentially a system health check (like running a virus scan on a laptop).
While a vulnerability assessment is often conducted as a mandatory exercise as part of complying with regulatory requirements, such as PCI DSS or ISO 27001, it is strongly recommended that vulnerability assessments are conducted regularly; on all new devices before deployment and again throughout the year (like a fire drill).
A penetration test is the difference between ‘ticking a box’ and being confident you have looked at your vulnerabilities from every angle. The testing is undertaken by humans who understand the nuances of how businesses work—unlike automated scanning software, they can ask questions when something doesn’t seem quite right (which is important for ongoing business operations).
Much like carrying out an annual service on your car, we recommend regular penetration testing for all businesses to ensure ongoing mitigation of risk; however, it is even more important if you’re introducing new technologies to the workplace, moving to the cloud, outsourcing IT, have experienced a breach in the past, or aren’t confident about your current security posture.
Read more about the pros and cons of penetration testing and vulnerability scanning.
Whichever you choose truly does depend on the asset being tested; if the asset is low value (i.e. compromise wouldn’t have a devasting effect on operations or reputation), then a vulnerability assessment is probably adequate. However, if the asset is high value (i.e. a breach or failure could cause operational disruption and revenue loss or reputational damage), then it becomes a prime target for threat actors who invest time into finding more sophisticated ways to compromise and gain access.
Both options will provide you with a detailed report explaining the findings, the criticality of the vulnerabilities, and present remediation advice. However, the vulnerability assessment report will not cover impact or exploit information, as this can only be gleaned by exploiting the vulnerabilities manually.
It’s important to remember that new vulnerabilities are discovered regularly, so whether you’ve decided that a vulnerability assessment or a penetration test is the best choice for your organisation’s needs, it should be repeated regularly.
Read more:How your IT department can get the most out of penetration testing
Penetration testing and vulnerability assessments are important parts of mitigating cyber risk. Our experienced Penetration Testers have worked across a range of industries, finding vulnerabilities that can easily be missed in web applications and IT infrastructure. Our team can also help you to ensure that your systems are configured securely.
Help your IT department secure your business and contact us to discuss how we can make the process easier.


70% of all cyberattacks in 2024 involved critical infrastructure. That stark statistic from IBM’s X-Force 2025 Threat Intelligence Index captures the scale of the challenge facing Critical National Infrastructure (CNI) operators today.

Every business should have a Cyber Incident Response Plan (CIRP). Every business that handles sensitive data, operates under regulatory requirements, or wants to protect its reputation needs one.

The NCSC’s Cyber Essentials scheme is getting a substantial update in April 2026. Of course, the core principles will remain the same, but there are some practical elements that will change the reality of achieving or renewing your Cyber Essentials Plus certification.