Emerging threats

We support organisations striving to build a trustworthy, safe online environment where users can engage authentically in their communities.
Cross-sector corporatesWe support international government organisations and NGOs working to provide infrastructure or improve the capabilities, security and resilience of their nation.
International programmes and developmentWe support commercial organisations operating in a digital world, seeking to protect their reputation and prevent business disruption caused by cyber attacks and compliance breaches.
UK government and public sectorWe support UK government organisations responsible for safeguarding critical infrastructure, preserving public trust, and maintaining national security.



Not a week goes by that we don’t see a headline in the press that mentions something along the lines of “sophisticated phishing attack” or “new phishing attack approach”. The thing is: as long as we continue to embed technological innovation into our processes and increasingly rely on them, threat actors are improving their own approaches and looking for the weaknesses.
A while ago, we came across this article about a new phishing kit that made life even easier for actors looking to fool internet users into giving up valuable information. It started an internal conversation about how we keep our phishing vulnerability assessments up-to-date with what cybercriminals are doing, and is it enough?
To make sure we’re providing our clients with realistic scenarios, we keep track of the latest scams in the media, in crime reports, and on the dark web. We also monitor attacks directed at our own systems and at third parties.
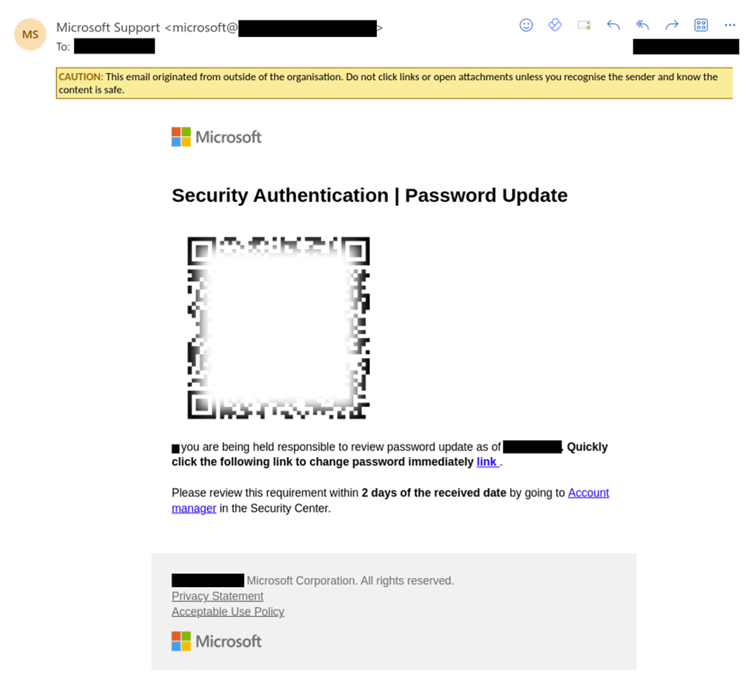
At the moment, we are seeing energy scheme scams, generative AI-supported scams, supply chain threats, and multifactor authentication threats. There has also been an increase in criminals targeting cloud credentials, correlating with the shift to hybrid working. For example, fake Microsoft 365 login pages that record credentials. These are not new approaches, certainly, but the volume of this has increased and will continue to do so as more and more organisations move to the cloud.
Then, when a client requests help in understanding how aware their staff are about phishing, we can take our knowledge of what threat actors are doing and apply it to that client’s specific situation—sector, size, processes and so on.
There are plenty of phishing campaign platforms out there that provide what we would call ‘off-the-shelf’ content. That might be a standardised email that is sent out to every employee with an email address. This is great for basic awareness, but it doesn’t account for the more sophisticated emails that come through—i.e. the ones that aren’t full of obvious red flags and have been heavily researched to increase the likelihood of the recipient clicking on a link or file e.g. those emails used for Business Email Compromise or spear phishing.
Here are some examples:
Generic email:
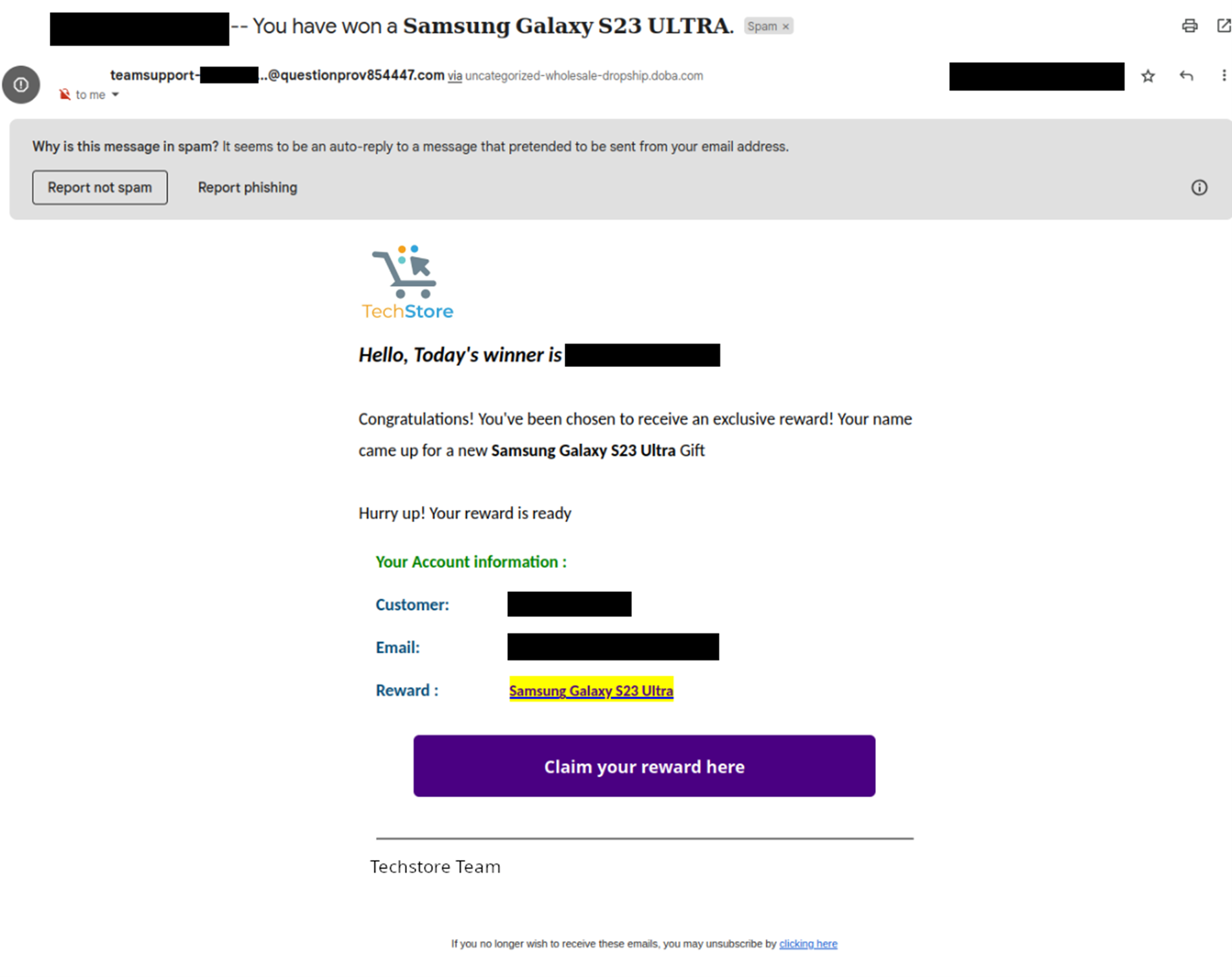
Researched Email:
While you may not have a lot of context, it’s clear that the sender of this email has made effort to research, so it looks legitimate e.g. addressed to a specific person about a specific task and mentions a current activity happening within the business.
Take the number of phishing approaches a cybercriminal could use and combine that with the very many different end users (in terms of both general technical skill and awareness) and you have a lot of variables in how your organisation could respond to the threat. There’s just no way that an off-the-shelf or templated phishing awareness solution can provide employees across such a broad spectrum with the tools they need to manage the risk appropriately.
In fact, we get very excited when clients ask us to make the campaign as difficult as possible because they know that threat actors aren’t going to hold back if they really want to succeed. In one instance, our client learned that:
Importantly, the point of a phishing assessment is to identify where further education is required. After clicking and entering information, employees at this organisation were provided with training that would enable them to spot phishing campaigns in future and how to best report to their security team.
Spam filters won’t identify every phishing email that comes through. And a big part of that is because cyber criminals are spending more time crafting their approach in order to get better results. As always, this means that humans are the last line of defence, so they need to be equipped to manage the risk, which includes being able to:
Do you know how your people would deal with a phishing email? Get reassurance that they will take the right actions and you are helping them to help you and themselves at work and at home.
Talk to us about Phishing Vulnerability Assessments and how we can tailor and time them to fit your specific requirements.
This article was originally published on 5 June 2021 and updated on 18 September 2023.

The UK Ministry of Defence (MoD) has introduced the new Defence Cyber Certification (DCC) scheme: a security framework for suppliers in the defence supply chain, designed to enhance overall resilience against cyber threat.

Social engineering attacks are on the rise and small and medium enterprises (SMEs) are especially vulnerable targets, often having more limited security resources and less mature defences that are easier to bypass.

PGI has officially been recognised as an Assured Cyber Advisor by the UK’s most trusted cyber security body, the National Cyber Security Centre (NCSC).